Recent data breaches at CircleCI, LastPass, and Okta highlight a recurring theme: the business SaaS stacks tied to these top-tier applications can be seriously compromised.
For instance, CircleCI plays a crucial SaaS-to-SaaS function in the creation of SaaS applications. Similar to this, for SaaS identity and access management, tens of thousands of organisations depend on Okta and LastPass security roles. Numerous unmonitored endpoints have been successfully introduced into organisations of all sizes by both enterprise and specialised SaaS apps.
SaaS security spending is increasing, although it is still less than other areas like network security and cloud infrastructure security. A glaring security hole in SaaS is caused by the average organization’s use of over 100 SaaS apps, many of which are not approved by IT.
Why Users Crush SaaS Apps and Frequently Ignore IT in the Process
The behaviours of end users have changed as productivity tools for jobs like marketing automation, document signature, and sales forecasting have moved from installed software to SaaS. SaaS solutions enable employees to do more tasks faster, especially in light of the growing decentralisation of the IT function.
Employees will always look for methods to use the tools of their choice to boost their productivity. Although this behaviour is not unusual nor malicious in and of itself, it raises serious security issues. Organisations implemented endpoint protection to workstations and devices in the era of installed software to prevent employees from downloading malicious software or falling prey to malware-based attacks. This strategy is still an important part of endpoint security overall, but it doesn’t take into account how people are working now, which is frequently outside of corporate networks and on personal devices.
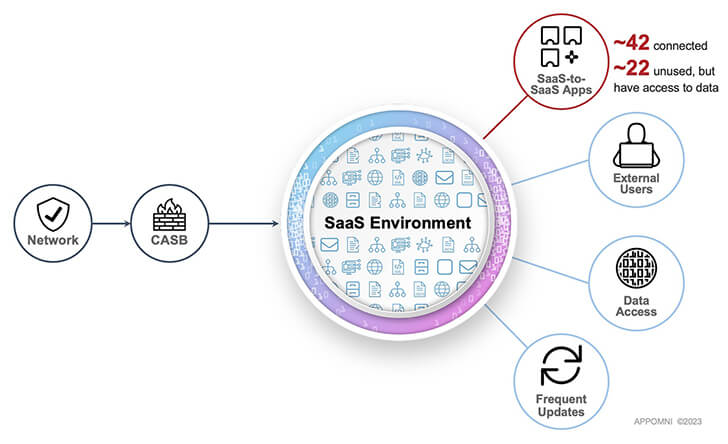
They pull out the credit card or choose a 30-day free trial of the SaaS apps rather than approaching Security or IT to grasp policies for onboarding new SaaS solutions and risking red tape, delays, or refusal for their requests. When workers approve linking their new apps to business SaaS systems like Microsoft 365, Salesforce, Workday, or ServiceNow, they seldom ever think about the security consequences of the shadow IT they have introduced into the ecosystem.
With no way to monitor or manage this attack surface risk, these connections, along with the users’ inherited permission settings, could have access to the organization’s most sensitive data. And it takes place each day.
Steps to Secure and Monitor SaaS Connections in Practise
The majority of security teams lack the necessary tools to monitor SaaS connectivity and the related user activities. These issues are addressed by SaaS Security Posture Management (SSPM) systems, which give the SaaS estate insight and control.
For example, SSPM can be used by an IT or security expert to find out what is running in Salesforce and what SaaS apps are linked to it. The same is true for the organization’s use of various additional SaaS applications.
The ongoing monitoring of SaaS apps and SaaS-to-SaaS connections now has more visibility and control, which lowers the danger of an attack surface and allows for proactive security control. The Security team can take action if a vulnerability is found, such as identifying unapproved, unsafe, and excessively-permitted SaaS programmes.
The Security team is in a position to establish a baseline of SaaS activity to utilise as a time-in-point frame of reference thanks to the continuous monitoring capabilities of an SSPM solution. Although the possibility of a SaaS-related compromise may never be completely removed, using SSPM greatly reduces that risk.
